Check our terms and conditions, privacy policies, and cookies policy.
Copyright 2024 © All rights Reserved. Designed by LACNet
As explained in Overview, the GAS distribution protocol is a layer designed and developed by LACNet to prevent DoS attacks and require writer nodes to sign the transactions they broadcast to the network so they can be made accountable for them. As in every GAS distribution protocol, there are always potential attacks to be carried out by malicious node operators or end-users. It is essential to be able to identify these attacks in order to mitigate them. With the help of Coinspect, the LACNet team has developed protocols to mitigate all potential following attacks from an end-user/application/end-service with access to a writer node or from a malicious writer node to the network.
By attacks to the network we are referring to any behavior than can impact the network negatively, including sending invalid transactions, attempting to modify Admin Smart Contracts (such as the Node Permissioning Contract, the RelyHub, or the Transaction Permissioning Contract) without permission, allowing non-permissioned nodes to broadcast transactions, attempting to use more GAS than the GAS limit available, attempting to attack other writer nodes or end-users by forwarding or overwriting pending transactions, or trying to overload the transaction pool of other nodes with transactions that will not be executed for different reasons. LACNet, as an orchestration vehicle, is responsible for ensuring that all these potential attacks are prevented or mitigated before they can impact the network.
The first and most basic attack that any malicious writer node operator or end-user/ application/service with access to a writer node can attempt is sending transactions that exceed the GAS limit assigned for that writer node in that block, which could lead to a DoS attack. Writer nodes would need to modify their signer in order to perform this attack because the signer is set by default to refuse sending transactions that overpass the GAS remaining in each block Solution-Architecture-Writer Node.
The GAS distribution protocol prevents the attack by banning the writer node as soon as the first transaction that exceeds the GAS limit is broadcasted. This ban consists of removing the writer node from the Transaction Permissioning Contract so new transactions will automatically be rejected by validator nodes. To be added back into the Transaction Permissioning Contract, the writer node operator needs to clarify the potential DoS attempt to the Permissioning Committee.
As the base technology of the LACNet Besu network is Ethereum, every transaction executed by the nodes involves a computational cost, which is measured in units of GAS. When a transaction is sent with insufficient GAS, the transaction will not be fully executed by the validators. This releases an out of GAS (OOG) exception indicating that there was not enough GAS to complete the full execution of the transaction.
A malicious end-user could send multiple transactions with a GAS limit lower than what the transaction actually requires for execution, thereby attempting to generate the OOG exception. When the exception is launched, it does not execute the step of GAS reduction in the GAS Management Smart Contract. This makes it such that a malicious end-user or node operator could evade the accounting of how much GAS the node has consumed in that block. This situation could incur a ban for the writer node operator if it leads to the writer node attempting to exceed its GAS limit.
This potential attack is prevented with a prior check by validator nodes against the Transaction Permissioning Contract that discards these types of transactions before they are executed. Prior to the execution of the transaction by validator nodes, validator nodes check against the Transaction Permissioning Contract to confirm that the GAS limit of the transaction, based on the amount of bytes sent, is higher than what will be required to execute the RelayHub contract. By doing this, we guarantee that the amount of GAS is sufficient enough to complete the execution of the RelayHub contract and ensure we account for the GAS used by the node that sent the transaction, as well as the OOG exception. In case the GAS limit sent in the transaction does not cover the RelayHub execution, the transaction is rejected prior to the execution, and thus, no computation is involved.
All transactions must go through the RelayHub contract before they reach their destination contract. A malicious user may want to re-enter the RelayHub contract with the intention of consuming GAS in a block without going through the accounting of the GAS protocol. The malicious user sends a transaction in which the target contract, after going through the RelayHub, becomes the RelayHub itself. This potential attack is prevented by the RelayHub by not allowing re-entry. The RelayHub would return an error and the GAS consumed by the transaction is discounted to the writer node.
A malicious user might want to modify admin contracts such as the Node Permissioning Contract, the Transaction Permissioning Contract, or the GAS Management Contract. For example, the malicious user would send a transaction in which the final destination contract after going through the RelayHub would be the method of removing nodes from the GAS Management Contract.
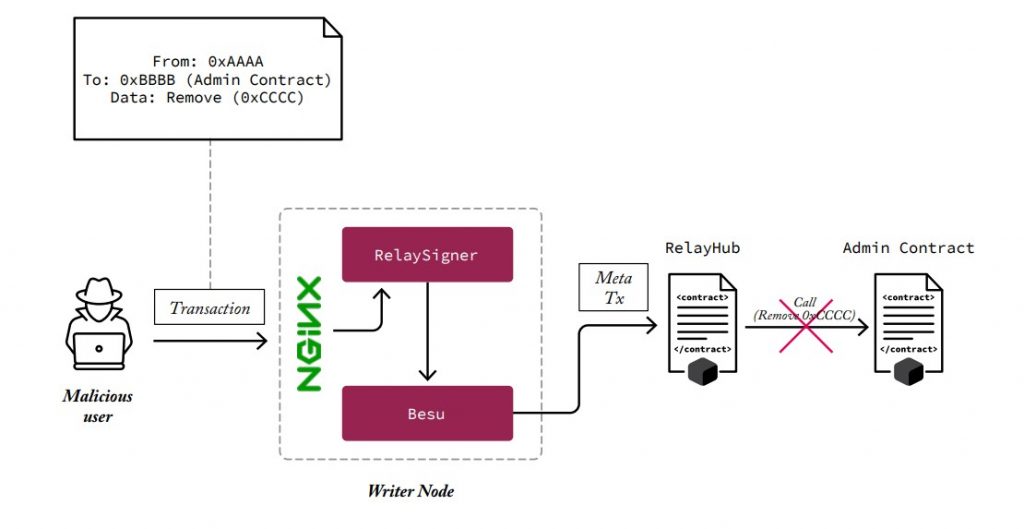
This potential attack is prevented by the RelayHub. When the validator nodes execute transactions against the RelayHub, the RelayHub confirms that the target contract is not any of the management contracts. This prevents end-users from reaching the contracts through the RelayHub, which has permission, through these contracts, to enable authorized users to interact with these contracts. Only authorized users specified in the RelayHub are allowed to interact with the Admin Contracts. Through this process, the malicious transaction would not be executed against the Admin Contracts and the GAS would be discounted to the writer node that broadcasted it.
LACNet networks are permissioned networks, which means that permission is required for the node to join the network and connect to other nodes in the network.This permission is based on a permissioning smart contract.The Permissioning Committee updates the smart contract every time a node is added o removed from the permissioning, and all the permissioned nodes accept or reject connections based on the list of nodes reflected in the permissioning smart contracts.
A malicious writer node operator could remove its default node’s permissioning settings (so it stops following the connections indicated in the Node Permissioning Smart Contracts), thereby accepting connections from new nodes. The malicious writer node operator would deploy a new malicious node or allow a third-party unauthorized node to connect to its node, allowing the unauthorized node or party to broadcast transactions that are replicated to the network by the permissioned node with the corrupted permissioning configuration.
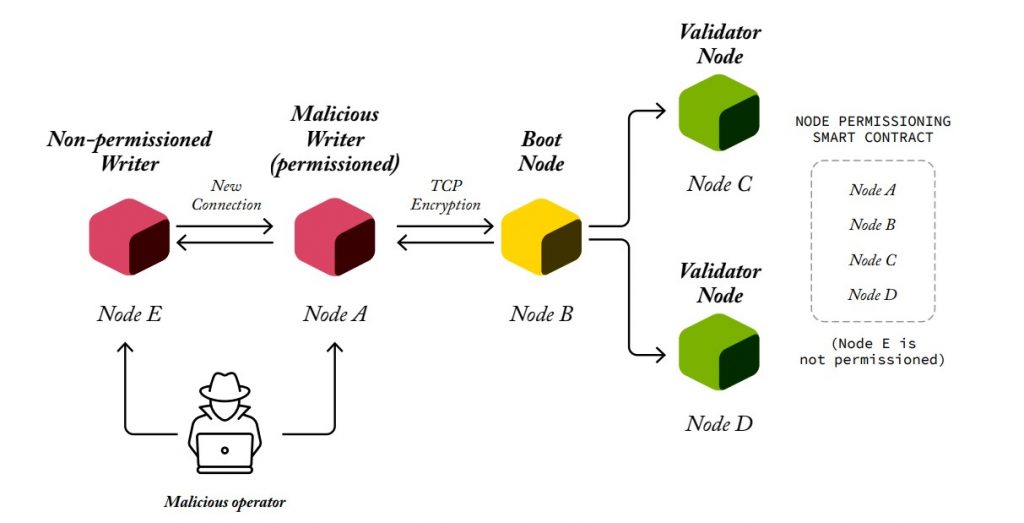
This potential attack is prevented by the Transaction Permissioning Smart Contract which rejects the transaction before it is execute because it is an invalid transaction as it is not signed by a permissioned node. The malicious node serving as a proxy will also be banned.
Check our terms and conditions, privacy policies, and cookies policy.
Copyright 2024 © All rights Reserved. Designed by LACNet